Top 10 Cyber Security Threats: Understanding the Risks and How to Stay Safe Online
What do you mean by cyber security threats?
Cyber security threats refer to potential risks or attacks that can compromise the confidentiality, integrity, and availability of digital information and systems. These threats can come in various forms, including malware, phishing, ransomware, data breaches, and more. In today’s digital age, where almost everything is connected online, it is crucial to be aware of these threats and take proactive measures to protect yourself and your data from cyber attacks.
How do cyber security threats affect individuals and businesses?
Cyber security threats can have devastating consequences for both individuals and businesses. For individuals, falling victim to a cyber attack can result in identity theft, financial loss, invasion of privacy, and even emotional distress. On the other hand, businesses can suffer from data breaches, financial loss, reputational damage, legal consequences, and disruption of operations. It is essential for everyone to prioritize cyber security to prevent such risks from materializing.
What is known about the top 10 cyber security threats?
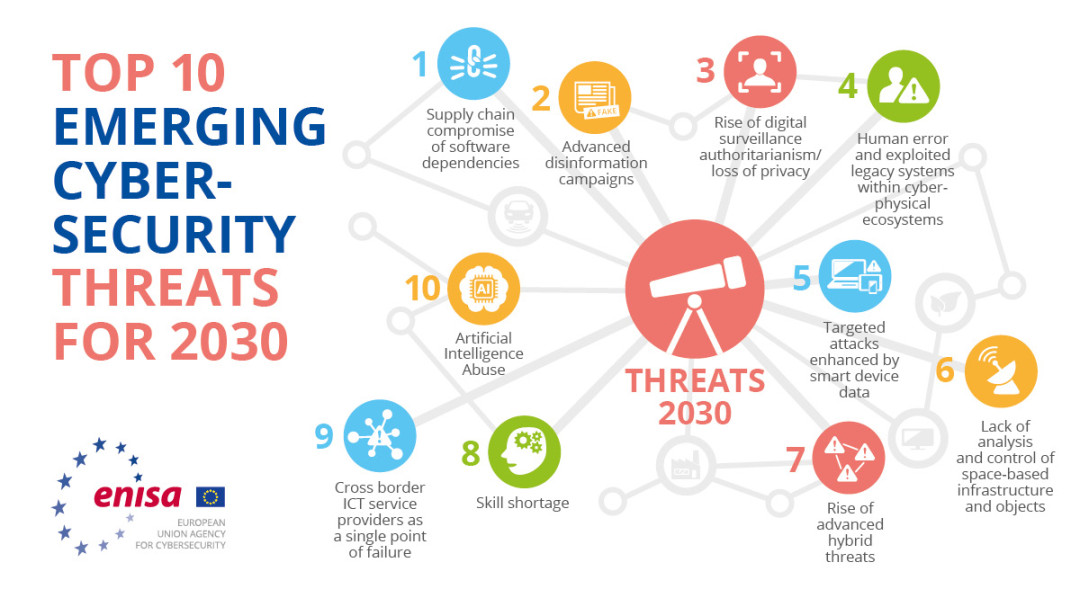
When it comes to cyber security threats, there are several common risks that individuals and businesses should be aware of. Here are the top 10 cyber security threats that are prevalent in today’s digital landscape:
1. Malware

Malware, short for malicious software, is a type of software designed to infiltrate and damage computers, networks, and devices. It can come in various forms, such as viruses, worms, Trojans, ransomware, spyware, and adware. Malware can steal sensitive information, disrupt operations, and cause financial loss.
2. Phishing
Phishing is a fraudulent practice where cyber criminals send fake emails or messages to trick individuals into revealing sensitive information, such as passwords, credit card numbers, or personal details. Phishing attacks are often disguised as legitimate communications from reputable sources, making it challenging to detect.
3. Ransomware
Ransomware is a type of malware that encrypts a victim’s files and demands a ransom in exchange for the decryption key. If the ransom is not paid, the files may be permanently lost. Ransomware attacks can be devastating for individuals and businesses, causing significant financial and operational damage.
4. Data Breaches
Data breaches occur when cyber criminals gain unauthorized access to sensitive information, such as personal data, financial records, or intellectual property. Data breaches can have severe consequences, including identity theft, financial fraud, and reputational damage.
5. Insider Threats
Insider threats refer to security risks that originate from within an organization, such as employees, contractors, or business partners. Insider threats can involve malicious or negligent actions that compromise the security of systems and data, leading to potential data breaches and financial loss.
6. DDoS Attacks
DDoS (Distributed Denial of Service) attacks involve flooding a target system with an overwhelming amount of traffic to disrupt or disable its services. DDoS attacks can render websites and online services inaccessible, causing inconvenience to users and financial loss to businesses.
7. Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks occur when a cyber criminal intercepts and alters communication between two parties without their knowledge. MitM attacks can enable attackers to eavesdrop on sensitive information, steal credentials, and manipulate data exchanges.
8. IoT Vulnerabilities
Internet of Things (IoT) devices, such as smart home gadgets, wearables, and industrial sensors, are prone to security vulnerabilities due to their interconnected nature and lack of robust security measures. IoT vulnerabilities can be exploited by hackers to gain unauthorized access to networks and devices.
9. Social Engineering
Social engineering is a tactic used by cyber criminals to manipulate individuals into divulging confidential information or performing certain actions. Social engineering attacks can be carried out through phone calls, emails, or in-person interactions, exploiting human psychology to deceive and exploit victims.
10. Zero-Day Exploits
Zero-day exploits refer to vulnerabilities in software or hardware that are unknown to the vendor and have not been patched. Cyber criminals can exploit zero-day vulnerabilities to launch targeted attacks before a security patch is released, making it challenging for organizations to defend against such threats.
Solution: How to protect yourself from cyber security threats
While cyber security threats are constantly evolving and becoming more sophisticated, there are several proactive measures that individuals and businesses can take to protect themselves from cyber attacks:
1. Keep software and systems updated
Regularly update your operating system, software applications, and security tools to patch known vulnerabilities and protect against emerging threats.
2. Use strong, unique passwords
Create complex passwords for your online accounts and use a password manager to securely store and manage your credentials.
3. Enable two-factor authentication
Add an extra layer of security to your accounts by enabling two-factor authentication, which requires a second form of verification in addition to your password.
4. Be cautious of suspicious emails and messages
Avoid clicking on links or downloading attachments from unknown or unsolicited emails, as they may contain malware or phishing attempts.
5. Backup your data regularly
Keep backups of your important files and data in a secure location to prevent data loss in the event of a ransomware attack or data breach.
6. Educate yourself and your employees
Provide cyber security training and awareness programs to educate yourself and your employees about common threats, best practices, and how to respond to incidents.
7. Implement network security measures
Deploy firewalls, antivirus software, intrusion detection systems, and encryption protocols to safeguard your networks and data from unauthorized access and malicious activities.
8. Monitor and analyze security events
Monitor your systems and networks for suspicious activities, security incidents, and breaches, and conduct regular security audits to identify and address vulnerabilities.
9. Develop a cyber incident response plan
Prepare and test a comprehensive cyber incident response plan to effectively respond to and recover from cyber attacks, minimize damage, and restore normal operations.
10. Seek professional help and support
If you are unsure about your cyber security posture or need assistance in securing your digital assets, consider consulting with a reputable cyber security firm or hiring experienced professionals to help you mitigate risks and strengthen your defenses.
Conclusion
Cyber security threats are a serious concern in today’s digital world, with individuals and businesses facing a multitude of risks that can lead to financial loss, reputational damage, and other consequences. By understanding the top 10 cyber security threats and implementing proactive security measures, you can better protect yourself and your data from cyber attacks. Remember to stay vigilant, stay informed, and stay safe online.
FAQs: Frequently Asked Questions
1. How can I tell if my computer has been infected with malware?
If you notice unusual behavior, such as slow performance, frequent crashes, or strange pop-ups on your computer, it may be a sign of malware infection. Run a reputable antivirus or anti-malware scan to detect and remove any malicious software.
2. What should I do if I receive a suspicious email asking for my personal information?
If you receive a suspicious email asking for personal information or financial details, do not respond or click on any links. Report the email as spam or phishing to your email provider and delete it immediately to avoid falling victim to a phishing attack.
3. How can I protect my IoT devices from cyber security threats?
To protect your IoT devices from cyber security threats, change default passwords, keep firmware updated, disable unnecessary features, and segment your network to isolate IoT devices from sensitive information and critical systems.
4. What are the consequences of a data breach for individuals and businesses?
For individuals, a data breach can result in identity theft, financial fraud, and emotional distress. For businesses, a data breach can lead to financial loss, reputational damage, legal consequences, and disruption of operations, affecting customers, partners, and stakeholders.
5. How often should I review and update my cyber security measures?
It is recommended to review and update your cyber security measures regularly, at least once a year, or whenever there are significant changes in your digital environment, such as new technologies, threats, regulations, or business operations.



